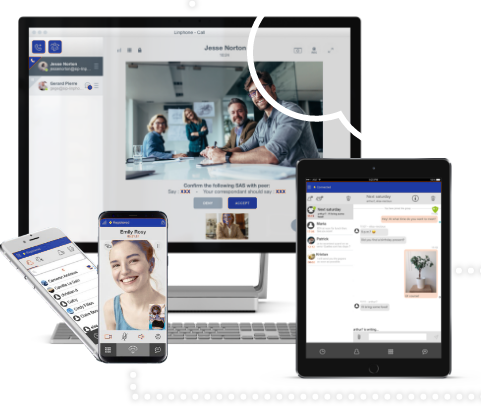
QTel™ is a massively secure private communications ecosystem that provides peer-to-peer encrypted voice, messaging, and video. Features include:
- Quantum-resistant encryption prevents man/machine-in-the-middle attacks
- Secure voice, video calls, and messaging (chat and text), including document attachments
- Each organization has its own private installation of peer-to-peer encryption to ensure security and privacy
- Hardened worldwide ecosystem supports mobile carrier networks, the internet, satellite networks, and broadband RF.
- No personally identifiable information (PII) or critical device information are collected (compliant with GDPR)
- No phone numbers (primary or secondary) are required
- Once users communicate, the record of the connection is purged and erased
- Available for Android, iOS, Windows, MacOS and Linux.